OBAKE SETUP CONFIGURATOR
GENERAL SUMMARY:

- This program is specific and restricted to the BUSINESS version of OBAKE.
- This program was created to authorize technicians from the Information Security area or other related sectors of the company, such as the Information Technology or Compliance/Auditing areas, to have access to the OBAKE RESTRICTED SETUP. Therefore, this tool allows the registration of authorized technicians to set the controls found there, with great security.
- The main objective is to provide an additional layer of protection with broad capillarity and mitigate, to the maximum extent, a leak that could allow someone to change key parameters of any OBAKE BUSINESS installed in your company. To accomplish this, it has several security features - which are not the subject of this manual.
OPERATION SUMMARY:
- Open the OBAKE SETUP CONFIGURATOR and inform the authorized password to create a new access. If no password is defined yet, the program will require you to define a new one.
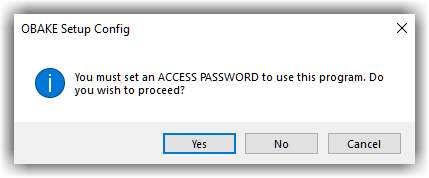
- Once the password is informed, the OBAKE SETUP CONFIGURATOR will inform the necessary steps to be performed by a new technician:
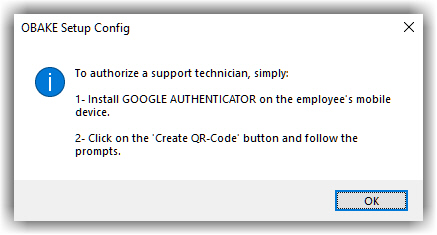
As seen, you will have only two steps to follow:
- Install the GOOGLE AUTHENTICATOR on the technician's cell phone. If the app is already installed, you can use it.
- Click on the "CREATE QR-CODE" button and follow the instructions.
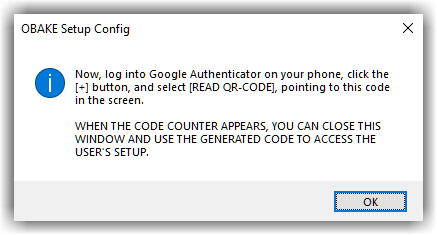
- After installing the GOOGLE AUTHENTICATOR, click on "CREATE QR-CODE", and the program will show the necessary steps to feed the Google Authenticator with the created code.

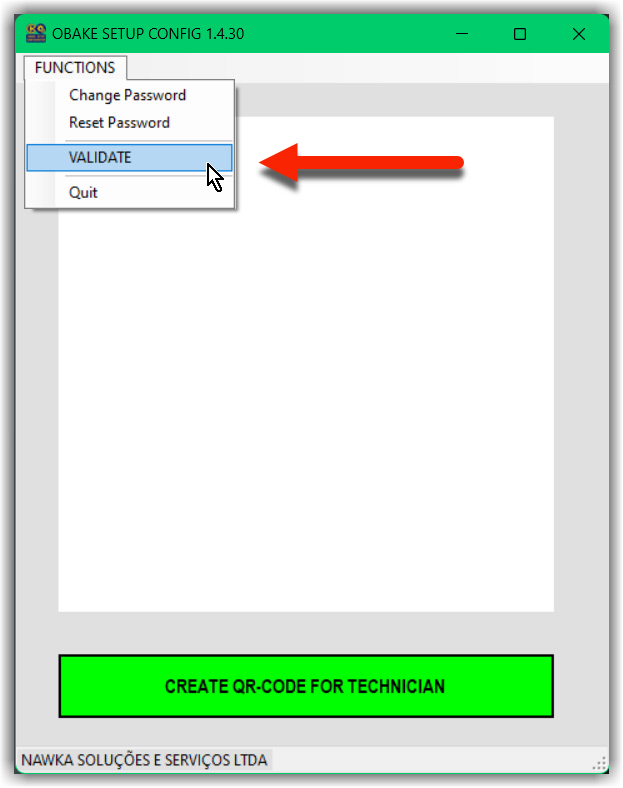
- After create the technician's access in his/her cell phone, we recommend to test the entire process. For this, choose the VALIDATE function in the main menu.
- You must inform the authorized e-mail and the current generated PIN in the GOOGLE AUTHENTICATOR.
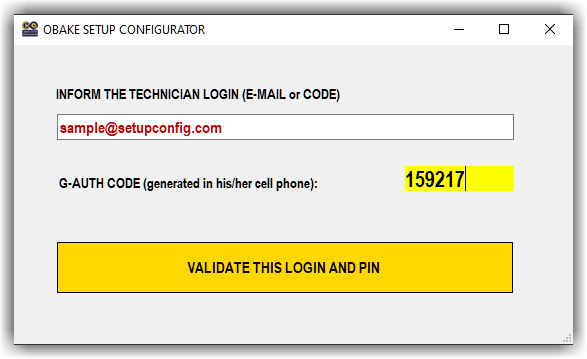
IMPORTANT: this code changes on each minute and the program has a tolerance around 30 seconds.
- If everything is 100%, a message will inform this ...
- .. otherwise, an error will be reported, indicating that the problem may reside in date/time differences between the cell phone and the computer you use to create the code. Therefore, BOTH must have the same date and time.

- After these steps, the technician is able to change the security features present in the RESTRICTED SETUP area.
