Security
Every aspects of Security can be handled and set here.
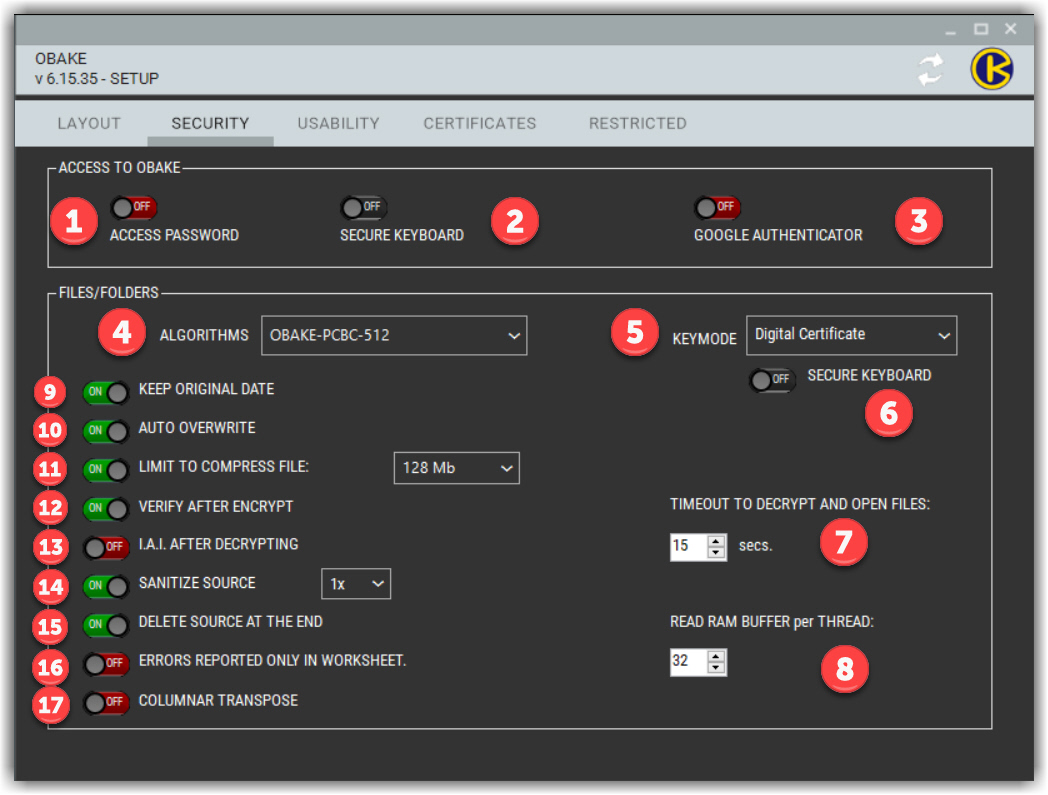
- ACCESS PASSWORD: if enabled, it will require a user-defined password for all OBAKE functions. It is highly recommended to prevent unauthorized use of OBAKE while working in an office or when OBAKE is installed on a laptop that may be lost or stolen.
- SECURE KEYBOARD: OBAKE offers a Secure Virtual Keyboard to strengthen the security during the input of PASSWORDS and SECRET-KEYS. This keyboard is 100% immune to software monitoring and creates an additional layer of protection. It allows users to input data by typing or, if wished, by clicking on each key - and in this case, there are secure effects to enhance its security level, like mixing all keys at each click and hiding all layouts on mouse hover. You can see a sample of its functioning in this video.
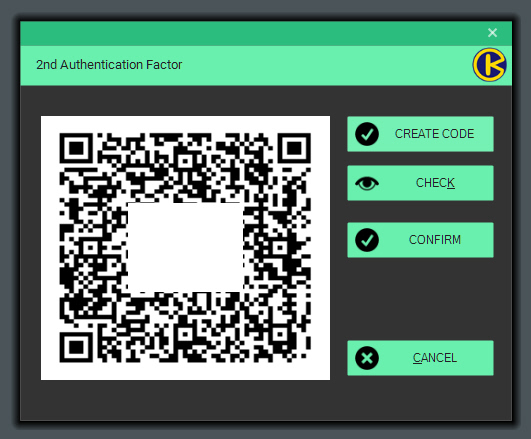
- GOOGLE AUTHENTICATOR: users can further enhance the security of using OBAKE through tiered authentications. This is known as "multi-factor authentication" since a 2nd or 3rd factor is required to authenticate their entry in a function. In this case, OBAKE provides Google Authentication as a new factor. Based on mobiles, it creates a unique number each minute, making it much more difficult for any invader to access OBAKE since he should know both PASSWORD and the UNIQUE-ID, present only in your mobile phone and valid for a single minute.
- ALGORITHMS: use this combo box to select a specific algorithm for encrypting your data. Remind that these algorithms may have different features indicated for different data types and file sizes. For a comparison between each one, please, take a look at this page.
- KEYMODE: use this combo box to select between SECRET-KEY (symmetric keys) or DIGITAL-CERTIFICATES (asymmetric keys).
- SECURE KEYBOARD: enabling this control will force OBAKE to utilize the SECURE KEYBOARD to get secret keys, independent of using it for passwords (see 2 above).
- TIMEOUT TO FASE: OBAKE allows you to edit any encrypted file quickly (see FASE). This time is necessary to indicate to OBAKE the timeout in cases where the file cannot be opened due to any issue, either on the file itself or in its associated application. Once the timeout is reached, OBAKE stops its file monitoring and indicates to the user the problem that had prevented the file from being opened.
- READ RAM BUFFER: OBAKE allocates parallel threads to speed up operations with big files, each with its dedicated RAM amount. So, here the user can indicate how many megabytes will be dedicated to each thread. TIP: This value may impact more or less depending on several hardware factors (like CPU, pipelines, disk types, total RAM available, RAM speed, etc.), and there is no rule about the optimized value. So, test it carefully, and we suggest using at most 64 Mb/thread due to some Windows Heap intrinsic.
- KEEP ORIGINAL DATE: if enabled, the encrypted file will keep the CREATED and MODIFIED dates of the source file(s). If disabled, the current date will be used for both (the default behavior of MS Windows).
- Auto-Overwrite: If enabled, the program will automatically overwrite all existing files. Whether disabled, OBAKE will force the user to confirm any overwrites, either in encryption or decryption operations, if an existing file is found.
- Limit to Compress File: if enabled, OBAKE will respect the threshold imposed by the combo box next to it to compress source files. Compression can reduce the size of the encrypted files, but on the other hand, it consumes time and resources for this operation. Notice also that OBAKE has an intelligent compression algorithm, automatically discarding all file types that are already compressed (like ZIP, RAR, and a few dozen other types).
- Verify After Encrypt: if enabled, it makes OBAKE verify all encrypted files after their encryption, avoiding problems related to hardware failures that could damage them. It is highly recommended that SANITIZE SOURCE or DELETE SOURCE are enabled. .
- IAI after Decrypt: if enabled, all decrypted files will be shown in the I.A.I. module to assure you of their origin, creation, modification dates, and authorized persons. If your OBAKE version is FULL, we recommend to keep it enabled; otherwise, we recommend disabling it, as you can inspect the files directly in the IAI module.
- Sanitize Source: if enabled, all source files will be destroyed (wiped) after the current operation to make it IMPOSSIBLE for anyone to recover the information. For more information about it, go to the SANITIZE topic. The user can also define the number of cycles of wipe operations in the combo box near it.
- Delete Source at the End: if enabled, it provides the deletion of the source file after a successful operation (encryption or decryption). Warning: simply deleting a source file does not ensure that the data will not be recovered, and if you want to use this feature, we recommend enabling SANITIZE too.
- Errors Reported only in Worksheet: if enabled, OBAKE will not pause on any error that occurred during operations in files (its default behavior), just reporting them in the GRID rows. It is advantageous during operations with a significant number of files..
- Columnar Transpose: for those especially worried about security, the algorithm OBAKE offers another layer of cryptographic security based on a very sophisticated "rail fence", which works with many rows and columns, randomly set per file. In adding this algorithm to the encryption performed with the algorithm OBAKE-512, security is greatly expanded, but at a proportional cost to the algorithm's performance. Note: it is exclusive to the OBAKE-512 algorithm.
