FILES & FOLDERS
NOTE: some sample screens below may have different colors and backgrounds (Dark or Light) to show that you can customize the program interface.
The FILES & FOLDERS interface allows you to change, on-demand only, any of the OBAKE security parameters (see SETUP - SECURITY) and you must change them BEFORE select any file or folder.
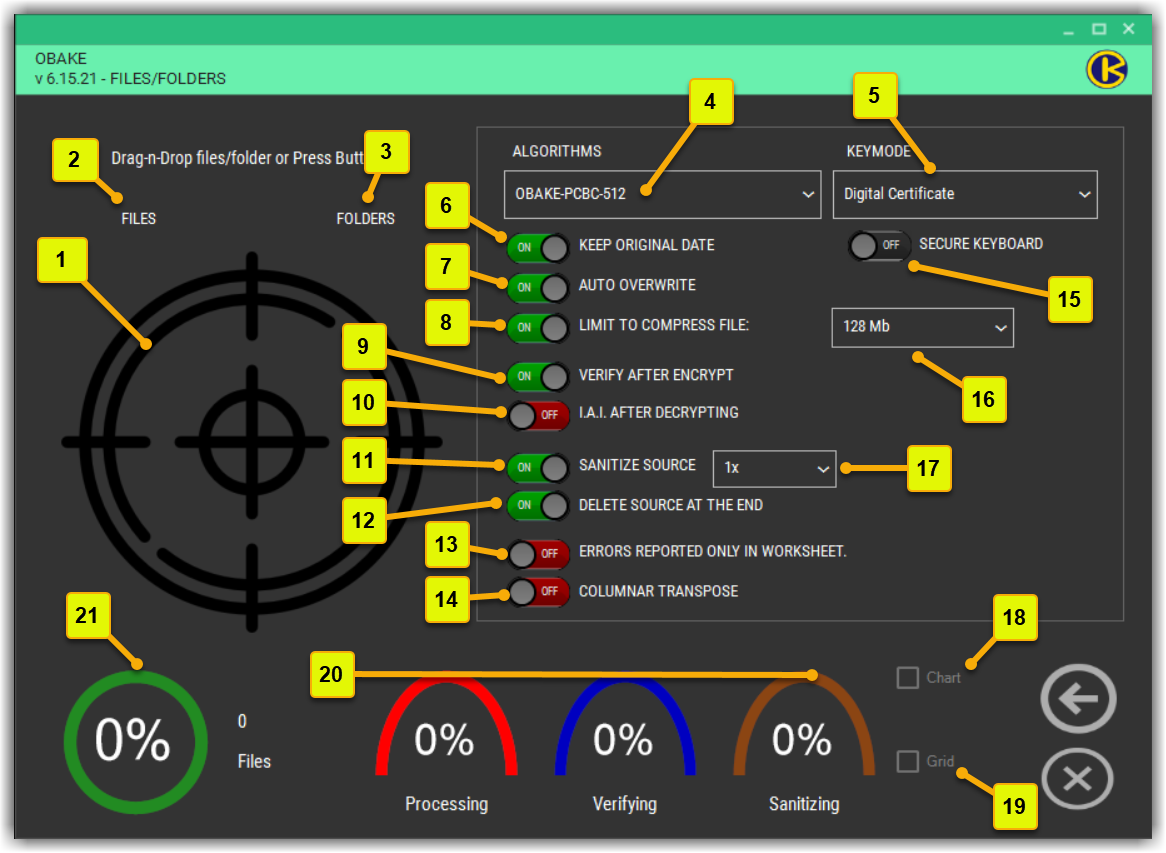
- Area for Drag-and-Drop files and folders: anything dragged into this area will be processed for encryption or decryption.
- FILES button: press this button to open an EXPLORER-like interface and select as many files as you wish (folders will not be selected) to be encrypted/decrypted. Only the selected files will be processed, and you can use the SHIFT and CTRL keys to select them, like in the FILE EXPLORER (Windows Explorer).
- FOLDERS button: as the same as the FILES one, this button allows you to select folders (and their sub-folders) to be encrypted/decrypted. Files will not be seen by this button, and be aware that all sub-folders will also be processed.
- Algorithms: use this combo box to select the encryption algorithm for encrypting your data. This selection has no effect during the decryption: OBAKE automatically detects the used algorithm in each file.
- KeyMode: use this combo box to select between SECRET-KEY (symmetric keys) or DIGITAL-CERTIFICATES (a type of asymmetric keys).
- Keep Original Date: if enabled, the encrypted file will keep the CREATED and MODIFIED dates of the source file(s). If disabled, the current date will be used for both (the default behavior of MS Windows).
- Auto-Overwrite: if disabled, it will force the user to confirm any overwrites, either in encryption or decryption operations, if an existing file is found. Whether enabled, the program will automatically overwrite all existing files.
- Limit to Compress File: if enabled, OBAKE will respect the threshold imposed by the limit (see topic 16) to compress source files. Interestingly, OBAKE has an intelligent compression algorithm, automatically discarding all file types that are already compressed (like ZIP, RAR, and a few dozen other types).
- Verify After Encrypt: if enabled, it makes OBAKE verify all encrypted files after their encryption, avoiding problems related to hardware failures that could damage them. It is highly recommended that SANITIZE SOURCE or DELETE SOURCE are enabled.
- IAI after Decrypt: if enabled, all decrypted files will be shown in the I.A.I. module to assure you of their origin, creation, modification dates, and authorized persons. If your OBAKE version is FULL, we recommend you keep it enabled; otherwise, we recommend you disable it, as you can look over the files directly in the IAI module.
- Sanitize Source: if enabled, all source files will be destroyed entirely (wiped) after the current operation to make it IMPOSSIBLE for anyone to recover the information. For more information about it, go to the SANITIZE topic. The user can also define the number of cycles of wipe operations - see the 17th topic for more details.
- Delete Source at the End: if enabled, provides the source file deletion after a successful operation. It acts on encryption and decryption operations.
- Errors Reported only in Worksheet: if enabled, OBAKE will not pause on any error that occurred during operations in files (its default behavior), just reporting them in the GRID lines. It is especially beneficial during operations in a considerable number of files.
- Columnar Transpose: for those especially worried about security, the algorithm OBAKE offers another layer of cryptographic security based on a very sophisticated "rail fence", which works with many rows and columns, randomly set per file. In adding this algorithm to the encryption performed with the algorithm OBAKE-512, security is greatly expanded, but at a proportional cost to the algorithm's performance. Note: it is exclusive to the OBAKE-512 algorithm.
- Secure Keyboard: if enabled, any PASSWORD or SECRET-KEY entry will be gotten in a genuinely secure virtual keyboard with unique characteristics. See this video for a better understanding.
- File Size Limit for Compression: if the COMPRESSION (8) setting is enabled, any file with its size equal to or smaller than the size set here will be compressed to reduce space and working time. Files that have already been compressed will not be processed.
- Here you can define the cycles of wipe operations (see topic 11 above), where each cycle is equivalent to 6 (six) different processes. The NIST recommends at least 7 (seven) cycles for Magnetic Disks (HDD), while for Solid Disks (like SSD or NVMe), it is recommended to make only one step due to the hardware intrinsic.
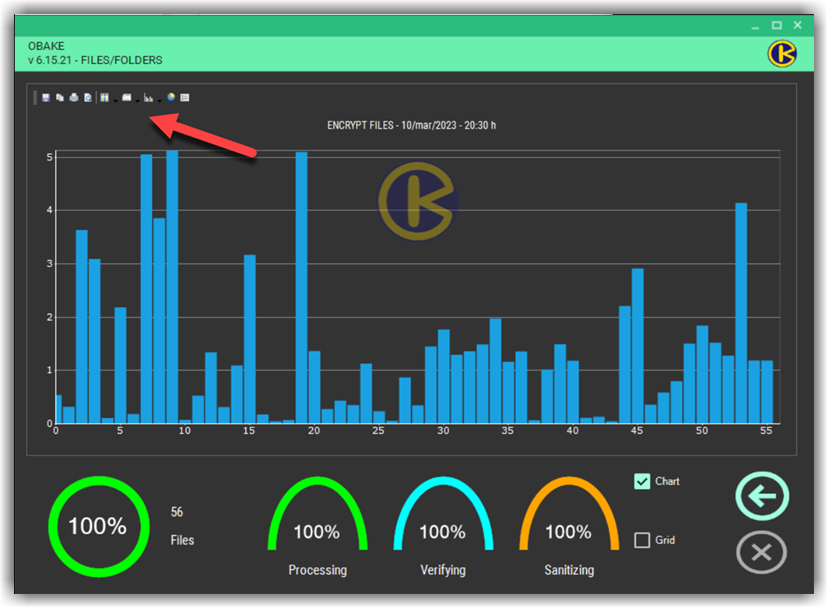
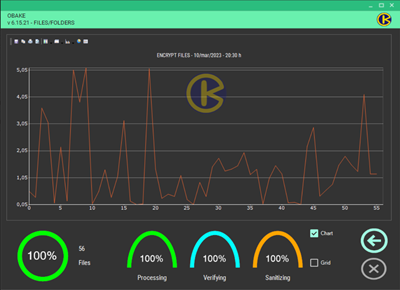
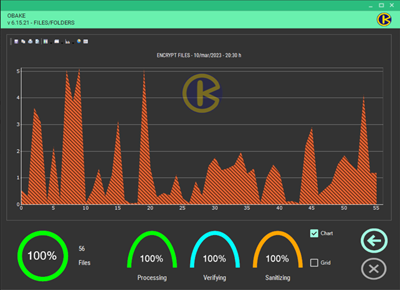
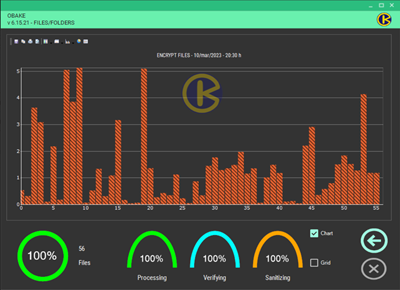
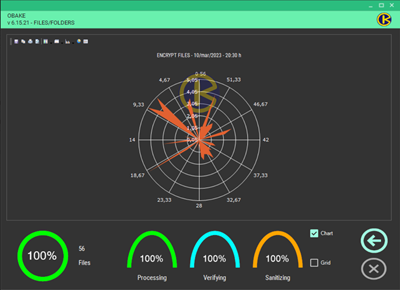
- CHART: if enabled, it displays the graph-based performance window. This window allows users to see the performance obtained in a bundle of files and print or save this information for Auditing or statistical purposes in a recurring environment (such as those used in backup plans). Many chart types are available, and users can still change their colors, lines, labels, etc. Here are some examples:
|
|
|
|
|
|
|
|
|
|
|
NOTE: if you don't need any chart information, we recommend you disable this window (uncheck CHART control in the SETUP - LAYOUT module) for performance gains.
- GRID: if enabled, it will show the GRID/WORKSHEET window that reflects all processed files and all the related data for each one:
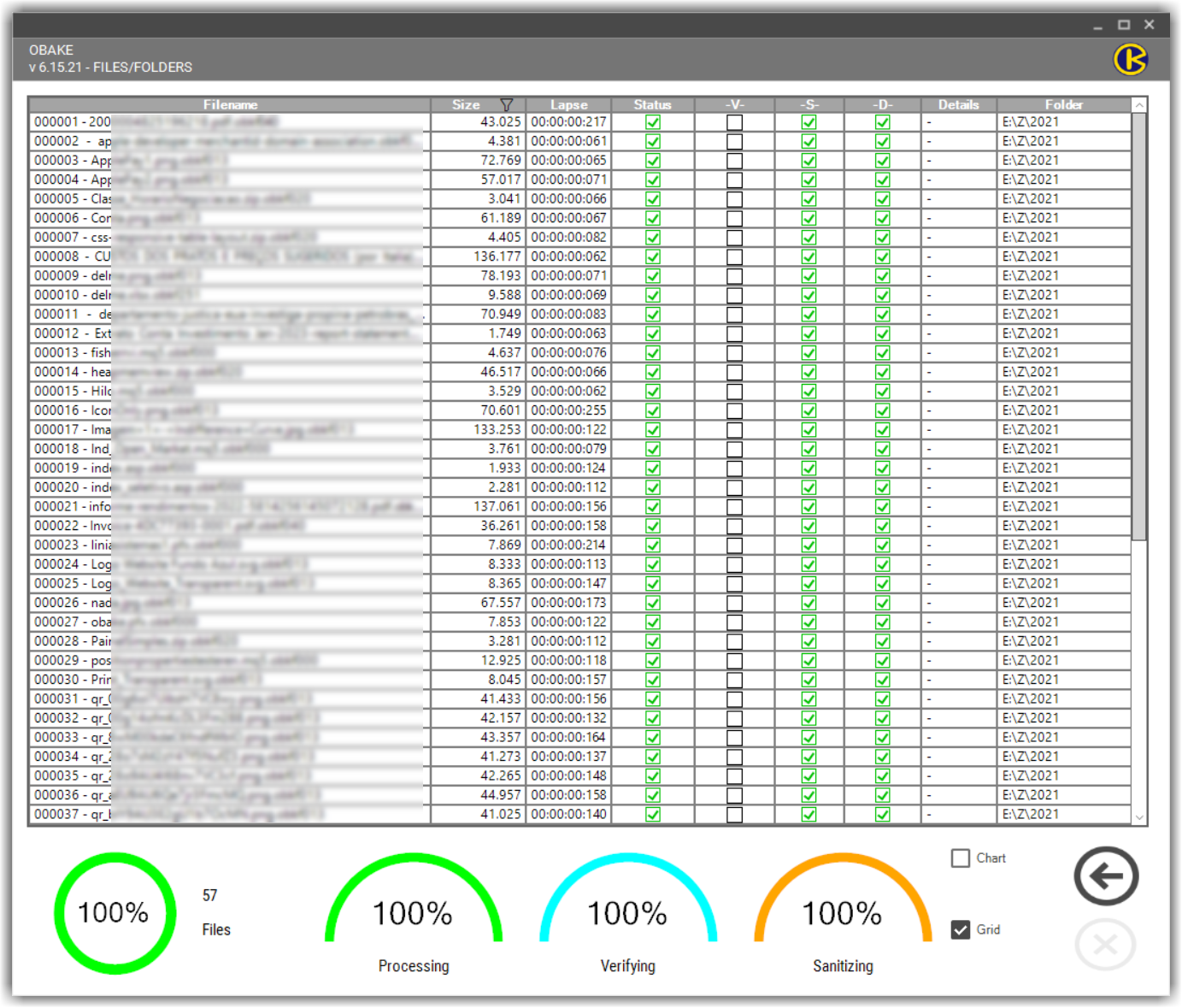
The GRID columns are divided as shown:
- FILENAME: this column shows the name and extension of each file, without the path information - this will be shown in a specific column.
- SIZE: this column shows the file size, in bytes.
- LAPSE: the elapsed time to process the file, expressed in hours, minutes, seconds and milliseconds.
- STATUS: if checked, everything went 100% with this file; otherwise, the flag will be unchecked and the column DETAILS will show what happened.
- "V" Column: it represents the VERIFY status of an encrypted file. It is related to encryption operations (only), and to the "VERIFY AFTER ENCRYPT" control (Topic 9).
- "S" Column: it represents the SANITIZATION status of an encrypted/decrypted source file. It is related to the "SANITIZE SOURCE" control (Topic 11).
- "D" Column: it represents the DELETE status of an encrypted/decrypted source file. It is related to the "DELETE SOURCE" control (Topic 12).
- DETAILS: if there is any error during the operation in the file, this column will expose the details about it.
- FOLDER: the complete folder path of the processed file.
- GAUGES: these are the indicators that show the three main operations of each file. They can be freely customized in the SETUP - LAYOUT module.
- GENERAL COUNTER: this gauge represents the general counter of the entire bundle of files.